On some level, the whole point of a security program is to manage risk. In securityprogram.io (SPIO) we provide policy around how the risk program should work and some templates for a risk management process that you can adopt as an organization.
On some level, the foundation of that is a willingness to document and talk about risks. The risk register helps you to do that. In theory, the idea is that anyone can report a risk that will get put in the risk register. In practice, it is often the technical team, security team or even users that report risks.
Once a risk has been reported, we track it in the register to help us document that we are aware of it and that we handled it. Often we use the risk register as part of our frequent discussion with broader management to make them aware of risks that we see and how we're dealing with them.
In SPIO, the risk register makes it easy to create and track risks. Then you can see who the owner is, start to estimate probability and impact and track the status, which is one of:
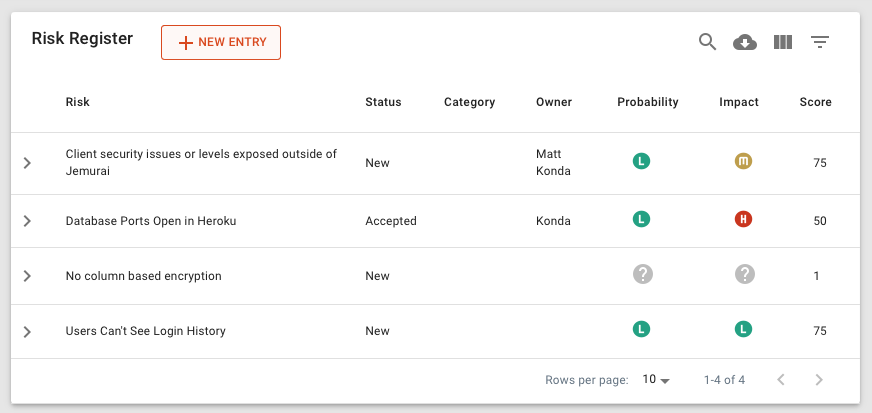
Risks in SPIO also have fields to gather:
Of course, it is helpful to understand when risks are identified and when they get handled.
It is a bad sign if risks are commonly identified but then there are long periods before they get handled.
It is probably a bad sign if there are no risks identified. That suggests that the organization doesn't have a very effective way to realistically identify and deal with risks.
If you are struggling to think about risks, a threat modeling exercise could be helpful. You can use our tool here to help with that: https://threatmodel.jemurai.com.
In the Assisted SPIO tier, our team will help to manage the Risk RegisterA risk register is a document or tool used by organizations to record, track, and manage risks associated with their operations, systems, or projects. A risk register typically includes a list of identified risks, their likelihood, potential impact, and risk mitigation strategies. and identify and track risks. We also conduct an annual deeper Risk AssessmentA cyber security assessment is a comprehensive evaluation of an organization's information technology systems, infrastructure, policies, and procedures to identify vulnerabilities and risks. The assessment can be performed by internal or external cybersecurity experts and typically involves reviewing policies, procedures, and training of personnel, analyzing security architecture and configuration, and testing security through simulations or real-world attack scenarios. where we look to make sure the overall program is aligned to your overall risk.
Ultimately, the Risk Register is just an easy way to center an organizational discussion around risk and track outcomes.
