Many of our securityprogram.io customers find us because they are being subjected to a larger company's vendor management process and they don't really know what to do.
One of our major goals as a company is to systematically help small cool innovative companies develop security maturity so that they can compete and win with bigger companies.
An important part of developing security maturity is managing your own vendors and the potential risks they introduce. In this post we'll talk about vendor risk, common processes for dealing with it and how we handle it in our tool.
Did you know that with SPIO Assisted, we can do vendor tracking for you?
Does anyone remember the Target breach disclosed in 2013? It stands out has being a very large breach (40M credit cards) but also for having been one of the first highly publicized breaches where the entry point turned out to be a third party HVAC vendor. This may have been the moment in time where attention started to more deeply focus on third parties.
The problem, of course, is that you can build a great system and do all the right things for security in your system and your code - but if you integrate with or build upon something that isn't secure, in many common cases, you inherit their weaknesses. People don't want to buy things that they could easily know are weak.
This has gone beyond being a Good Idea™ and become something more like a mandatory minimum bar for doing business with most bigger companies.
We have seen all kinds of risky vendors:
The first step in dealing with vendors is to figure out who your vendors are and how you should track them. We often ask finance for a list of vendors. Then we try to get pulled into procurement processes so that we'll know that a vendor is being vetted and onboarded by the accounting team.
You wouldn't believe how common it is that organizations use vendors without realizing it. Maybe someone in engineering set up a "free" account. Maybe someone in IT paid for a backup service with their company credit card. Getting a handle on who your vendors even are can be trickier than you might think.
Once you know who your vendors are, you need to think about what you need to know about them. Do they handle your most sensitive data? Do they handle it carefully? Do you need an audit to confirm that they do?
The diagram below illustrates an example flow chart you could build for your vendor management program.
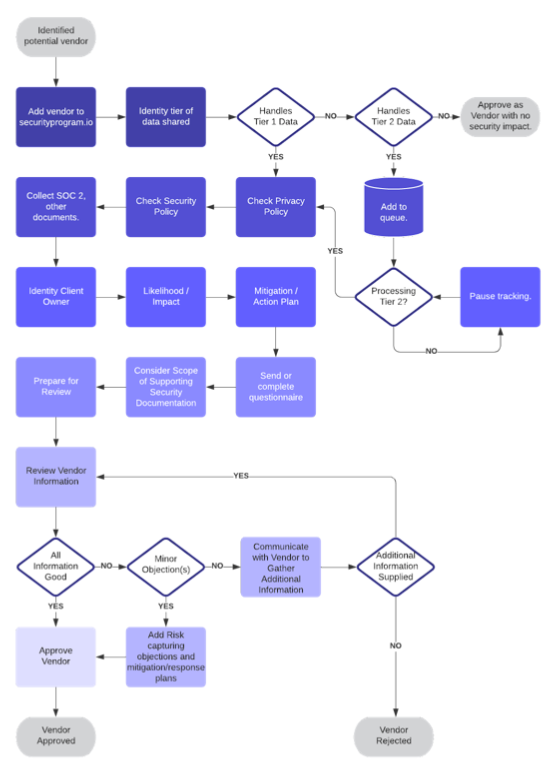
One way to help make sure you are doing the right diligence on vendors is to use an application to help structure the process. That's why we build a vendor management module into securityprogram.io.
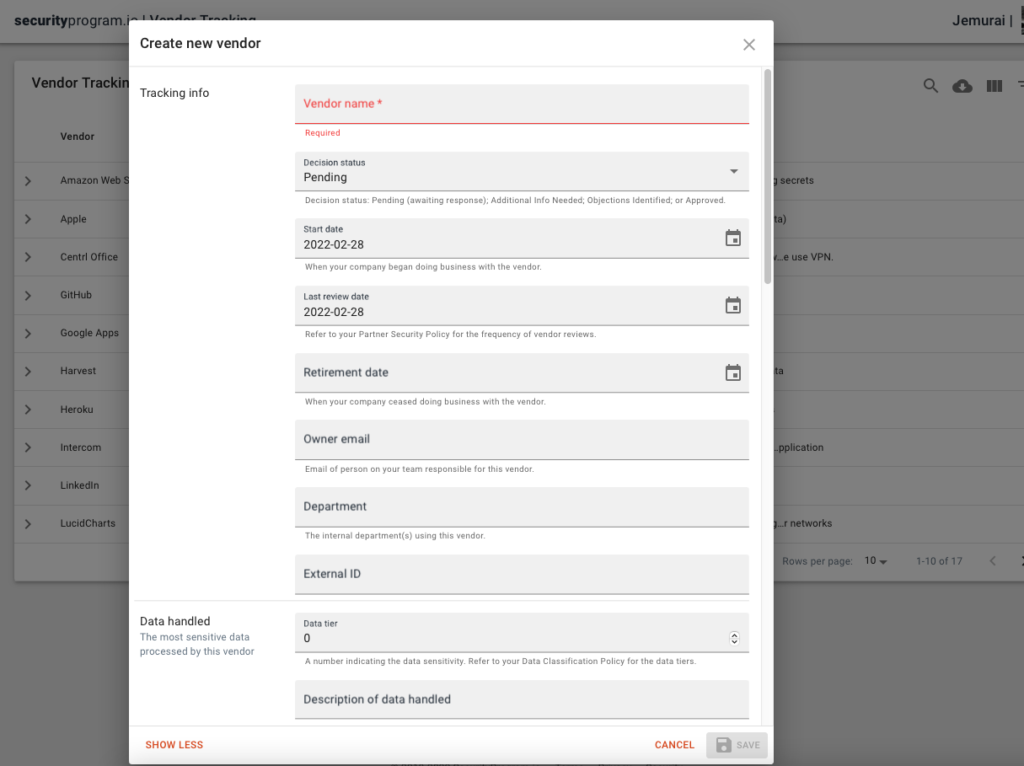
The Vendor Tracker makes it easy to:
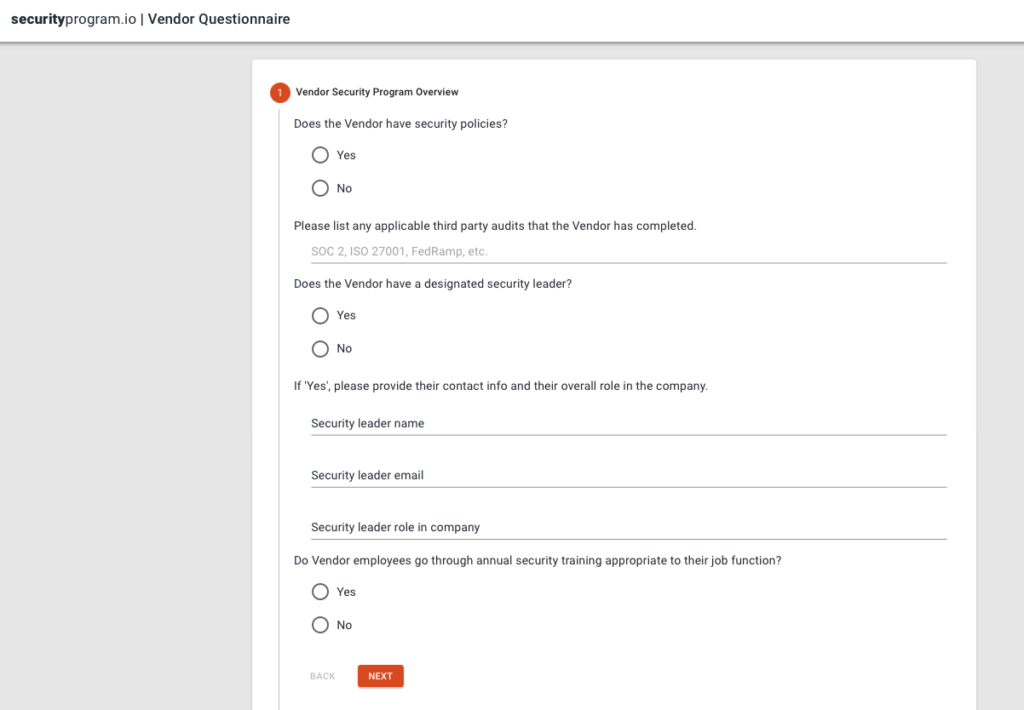
In the big scheme of things, Vendor Tracking is a pragmatic and minimal feature in SPIO. There are platforms you can buy that make it easy to administer very complex vendor management programs. We are not trying to compete with those, but to give smaller companies the basics that they need.
In the Assisted Tier of SPIO, our team helps you with vendor management. This ensures that your process is consistent and effective. It also makes it faster because many of our clients use the same vendors, so we don't necessarily have to do a full deep dive on diligence for every one of them.
For this to be effective, we still need to get plugged into your procurement process so that we know that a vendor is being onboarded, or renewed. But once we know that, and how they are being used, we can do most of the evaluation on our own. This can be a major time saver for our customers.
We tried to make vendor tracking as simple and pragmatic as possible. Whether you have us help you, or you do it yourself, the tools are right there for you.
