PhishingPhishing is a type of social engineering attack in which attackers use fraudulent emails, text messages, or other forms of communication to trick individuals into providing sensitive information or performing actions that can compromise their security. is where someone, typically some sort of organized cybercrime gang, sends a malicious email to a large group of people hoping that someone will respond, click a link, open an attachment or something like that. The objective is typically to compromise credentials or the user's computer.
Spearphishing is where such a campaign is conducted in a more targeted way, typically focusing on specific people with more personalized context that would make the campaign more compelling. WhalingWhaling is a type of cyber attack that typically targets high-level executives within an organization using social engineering techniques, such as email phishing or the use of malware. The goal is to obtain sensitive information or gain unauthorized access to systems and networks. is where spearphishing targets executives (think whale == big fish)! A common spearphishing or whaling objective is to get a financial officer or accounting team member to transfer money or change account details so that payments get misrouted.
What we have been seeing lately are campaigns that are conducted at a larger scale that is likely highly automated, but that also have the context required to be compelling and a request that is possible for many tiers of employees (not just finance execs) to do. We also got targeted directly by one of these, so we can share the detail. Let's do it!
SmishingSmishing is a type of social engineering attack in which an attacker uses SMS (Short Message Service) or text messages to trick users into divulging sensitive information or installing malware on their mobile devices. Smishing messages may appear to be from a trusted source, such as a bank or social media platform, and may include links or phone numbers that the user is prompted to click or call. is where someone is doing phishing (communications with malicious intent) over SMS or text messages. Our particular text looked like this:
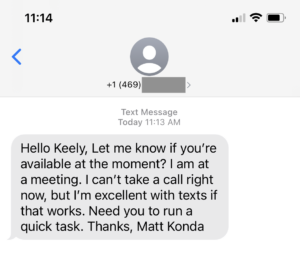
In this case, there are a couple of obvious things to note about the Smish.
Now in this case, we're lucky, Keely is on the ball and immediately realized that this wasn't real. It might have been the:
I'm excellent with texts ...
Phisher #1
There are some obvious other tells that we should call out:
Keely didn't respond, so we can't say for sure what would have happened next. However, we have seen this play out with customers with the exact same text (the "I'm excellent with texts" is hard to miss!) but from the customer CEO to an employee. When the employee responded, the campaign asked the employee to purchase Google Play gift cards.
Note that we have also seen other SMS campaigns and even more classic social engineering campaigns (phishing) to get people's phone number that were later used in an SMS campaign like this.
Based on what we are seeing, either this gang is particularly motivated and have time on their hands to do their research, or there are various layers of automation involved.
My guess is that they are using data from a LinkedIn data breach to associate people to companies, grab the company names, the people names, the phone numbers and emails and be able to formulate a programmatic automated but still targeted (contextual) campaign.
A particular interesting characteristic is using the CEO as protagonist in texts. It is common to see this used when an account has been hijacked to do the same thing, but maybe because not everyone has the CEO's real cell phone number it isn't always obvious that it isn't coming from them? SMS doesn't have the context (eg. signature, logo, etc.) that email does. Then again, with the data from LinkedIn (or whatever it is) the attacker could probably make a fake signature that looks pretty realistic substituting title, role, company, logo, etc.
Note that we have also seen other SMS campaigns that are similar in the sense that they use the CEO role but different types of messages - sometimes even targeting NEW employees.
Of course there are also the standby classic social engineering campaigns (phishing) to get people's phone number that were later used in an SMS campaign like this.
Educating employees about social engineering like phishing and smishing is a key part of a security program and can be one of the most important things you can do. We want employees:
SPIO can help provide this training. One of the customers that was targeted said that it was our training that made them stop and not follow through.
... your training was spot on in triggering all of the necessary awareness for me to start varying this exchange
SPIO User
