In security we talk a lot about understanding risk. That informs the advice we give and decisions we make. A tool I like to use for brainstorming about risk is a threat model in the form of a mind map. It is a simple starting point for thinking about threats.
In this post, we’ll talk about the new simple tool we released and how we use it.
Some threat modeling techniques (see references) can be very thorough and rigorous to implement. This is good if your team has the time and resources to do this, but it can be challenging if you don’t have dedicated resources that really understand the methodology.
We tend to start with a simpler mind map and store it with the developer’s project artifacts. OWASP’s
Threat Dragon does this, as does Threagile, but for various reasons we just like the flexibility of an
open ended mind map.
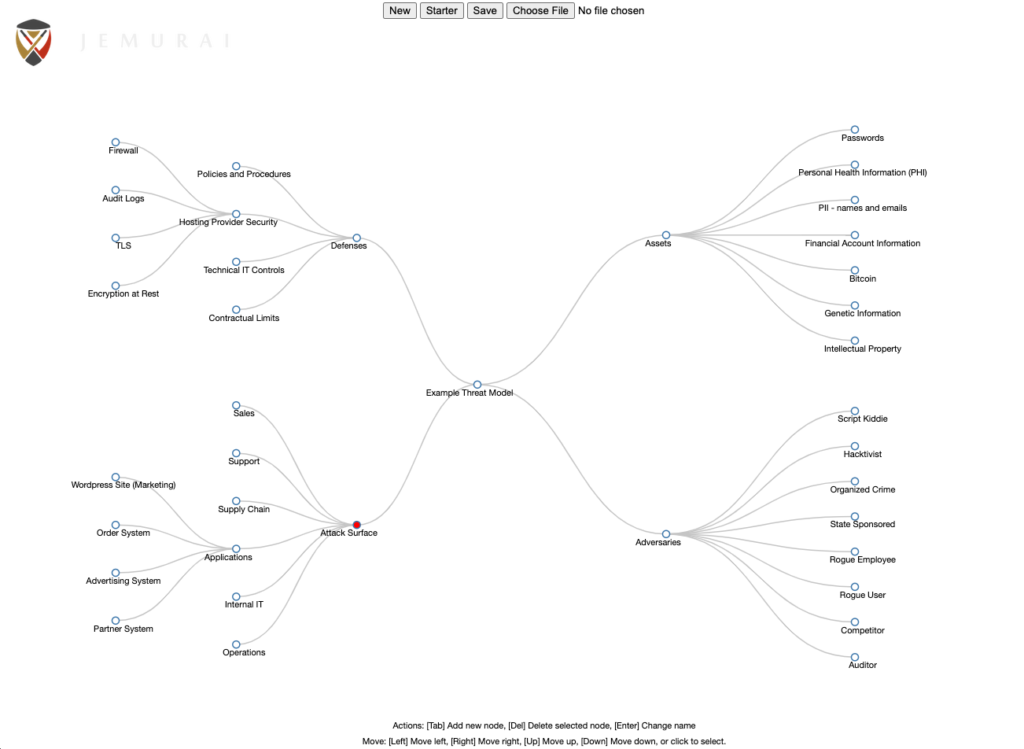
The process we use starts with preseeded model. We might build out more detailed examples of these, but as you can see from the screen shot above, we have preloaded:
We don’t aim for perfection. Maybe the first step is getting everyone on the same page about what our assets are!
The process is iterative and evolves. That’s one reason the tool allows you to build a model and then save it to a local JSON file. You can just put this in your source project and then open it later to see it again or make adjustments.
This is still very much brainstorming territory. We’re trying to come up with realistic threat scenarios.
To support this, we started with a simple D3.js project that does generic mind mapping and set it up with some preloaded data and hosted it here: https://jemurai.github.io/threatmodelmindmap/.
Note that this is a static site. The tool runs completely in your browser. We don’t know what your data looks like or have any information about what you do with it.
The tool basically lets you add nodes, rename them, delete them and navigate based on arrows and take action based on keys:
It also lets you preload a starting model. We are thinking we may try to capture some additional starters and add those so that people can get a running start on different scopes of models (eg. organizational, network, application, cloud env, business process, etc.).
To be quite honest, the tool should work for doing simple mind mapping totally unrelated to threat modeling too. We didn’t want to start out with too many assumptions about how it would be used.
Although we like the simplicity of the current tool, we have some ideas for extending it.
We would like to add additional template models that can be adapted for more specific scenarios. Basically to help people think about risk more proactively by preseeding the models with things they may care about.
We have also thought about bridging into a more quantitative model as a resulting step from the initial mind map. Imagine that we could create a row in a risk table for every combination of leaves in the different trees.
We might see an adversary targeting an asset via a part of the attack surface and we can then provide some level of calculation around that to think about risk more quantitatively. The quantitative part is hard to get right (kudos to FAIR) but with a decent UI, the mindmap provides the structure for the taxonomy and maybe makes the risk calculation more accessible.
| Adversary | Asset | Attack Surface | Records | Probability | Impact | Aggregate | Risk |
|---|---|---|---|---|---|---|---|
| Organized Crime | Financial Account | Partner System | 10,000 | 5% | 100 | 50,000 | Low |
| Organized Crime | Financial Account | WordPress Marketing Site | 0 | 10% | 100 | 0 | Low |
| Organized Crime | Financial Account | Order System | 1,000,000 | 2% | 100 | 2,000,000 | Medium |
| Organized Crime | Financial Account | Advertising System | 0 | 5% | 100 | 0 | Low |
| Rogue User | Bitcoin | Internal IT | 1,000,000 | 5% | 100,000 | 5,000,000,000 | High |
| Rogue User | Passwords | Order System | 1,000,000 | 2% | 10 | 200,000 | Low |
This model includes additional information like records, probably, impact, aggregate and a risk score. You can see that it helps us zoom in on the systems and data that really matters.
We have also imagined a way that a user could click on different nodes in the mind map and essentially map out the most important attack trees and create vectors:
The current model doesn’t support either of these, but we are putting thought into how they should work. We would welcome input here!
Note that the threat modeling tool is built upon open source work by folks we’d like to thank:
Michael Bostock for the D3.js framework and key examples.
Jeremy Darling who’s mindmap example was where we started.
Here are some good general Threat ModelingThreat modeling is a process for identifying and analyzing potential threats and vulnerabilities to a system, network, or application. It involves identifying the assets that need protection, determining the possible threats and attack vectors that could be used to compromise those assets, and assessing the likelihood and potential impact of each threat. references: